OsCommerce Malware Infection
Three months ago is started a huge site infection campaign with lens oscommerce, a famous cms for medium/little on-line stores. This cms suffers of few vulnerabilities that can lead an attacker to upload files and execute remote code.
Vulnerabilities:
- osCommerce 2.2 Remote File Upload Vulnerability
- osCommerce authentication bypass
- osCommerce 2.2 Arbitrary PHP Code Execution
- osCommerce 2.3.1 Remote File Upload Vulnerability
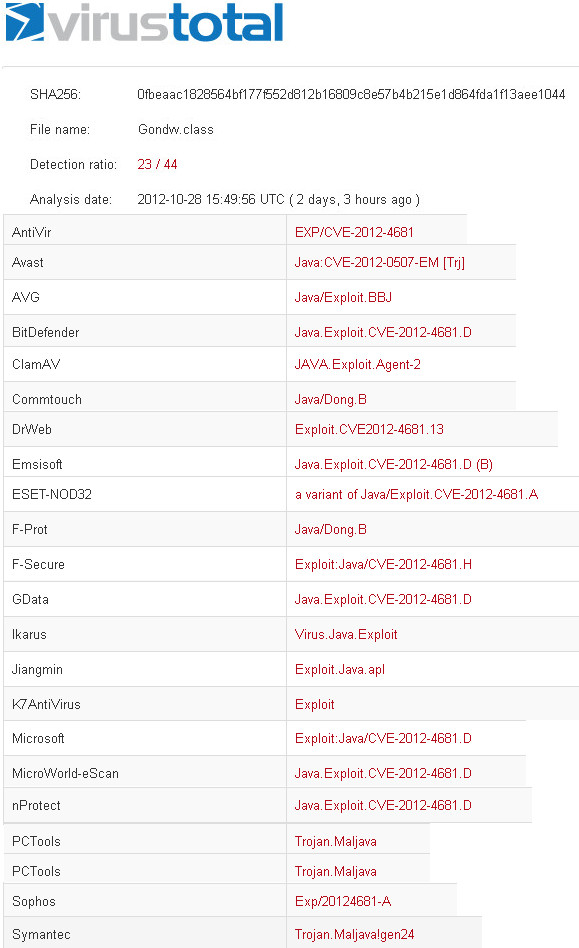
Today (4/10/2011) the total number of infected sites is 830,000 but two months ago was 8 million.
In some compromised sites the attacker has left the webshell.
After uploading a backdoor the attacker edit the home page and add a script/iframe tag that load multiple browser exploits.
Exploits used:
- IE 6 Remote Code Execution
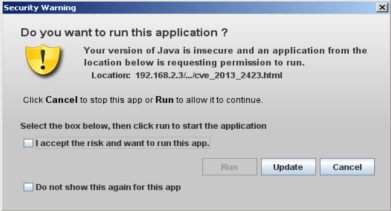
- Java Runtime Environment Remote Code Execution Vulnerability
- Microsoft Windows Help
- Adobe Reader and Acrobat 8.x
After successful exploitation a malware is downloaded and executed.
Scenario:
- 192.168.2.13 ----> Attacker with BackBox 2.0
- 192.168.2.7/os/ -----> Victim with osCommerce 2.2
- http://coolsite.dot ----> Malware host
- jquery.js (IE 6 Remote Code Execution CVE-2006-0003)
- windows.exe (windows calculator with reverse meterpreter tcp payload)
Steps:
What i want to show you is how probably an attacker has infected a site running an old copy of osCommerce to spread malware. These are the steps to follow:
1- Find a place where we can host our malicious code so we need to find a server with weak ssh/ftp password (coolsite.dot).
2- Create our malware injecting a meterpreter reverse payload into calc.exe and encoding it 3 times using shikata_ga_nai.
3- Waiting the connection back.
4- Upload malware and exploit to coolsite.dot.
5- Waiting for a victim.
6- Do what you want.
After obtaining the meterpreter shell we start the keylogger to steal gmail login credentials.
Reference and more detailed information:
- Willysycom mass injection ongoing
- Metasploit Unleashed
Vulnerabilities:
- osCommerce 2.2 Remote File Upload Vulnerability
- osCommerce authentication bypass
- osCommerce 2.2 Arbitrary PHP Code Execution
- osCommerce 2.3.1 Remote File Upload Vulnerability
Today (4/10/2011) the total number of infected sites is 830,000 but two months ago was 8 million.
Exploits used:
- IE 6 Remote Code Execution
- Java Runtime Environment Remote Code Execution Vulnerability
- Microsoft Windows Help
- Adobe Reader and Acrobat 8.x
After successful exploitation a malware is downloaded and executed.
VIDEO EXAMPLE
Scenario:
- 192.168.2.13 ----> Attacker with BackBox 2.0
- 192.168.2.7/os/ -----> Victim with osCommerce 2.2
- http://coolsite.dot ----> Malware host
- jquery.js (IE 6 Remote Code Execution CVE-2006-0003)
- windows.exe (windows calculator with reverse meterpreter tcp payload)
Steps:
What i want to show you is how probably an attacker has infected a site running an old copy of osCommerce to spread malware. These are the steps to follow:
1- Find a place where we can host our malicious code so we need to find a server with weak ssh/ftp password (coolsite.dot).
2- Create our malware injecting a meterpreter reverse payload into calc.exe and encoding it 3 times using shikata_ga_nai.
3- Waiting the connection back.
4- Upload malware and exploit to coolsite.dot.
5- Waiting for a victim.
6- Do what you want.
After obtaining the meterpreter shell we start the keylogger to steal gmail login credentials.
Reference and more detailed information:
- Willysycom mass injection ongoing
- Metasploit Unleashed




This comment has been removed by a blog administrator.
ReplyDelete